Food Defence Threat Assessment Template & Video Guide
Meeting the requirements of FDA - IA Rule, GFSI Recognised Certification Programmes, e.g. BRCGS, SQF, FSSC22000 and others
Save yourself and your food defence team hours and hours of discussions and brainstorming, and avoid potential confusion too!
You will get a food defence plan example, a 30-minute video guide, a food defense risk assessment matrix, the template and the mitigation plan.
Note: These guides and templates are provided and thoroughly discussed in Food Surety's Course: Developing & Implementing Food Defence Plan - TACCP.
What's included in this food defence mini course and TACCP template?
Templates
-
Draft policy for your QMS/FSMS (Word file)
-
Step-by-step food defence process guide (PDF file)
-
Complete Excel workbook food adulteration threat assessment and mitigation Template
Comprehensive Guide/Demo
White Label Templates
Embedded tips and explanatory notes.
Discussion Board
Food Defence & Site Security Training
Food Authenticity / Food Fraud Prevention Training

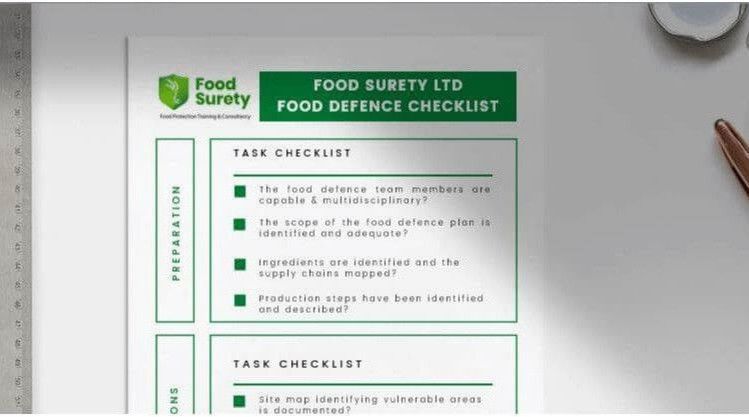
Food defence threat assessment template, editable Excel workbook satisfying FDA IA Rule, New Zealand MPI and GFSI recognised programmes requirements.
What makes an excellent Food Defence threat assessment and mitigation plan?
Systematic
- Identifies relevant products, sites, and supply chain potential threats
- Prioritise food defence threats using a systematic method like: simple quadrant risk matrix, CARVER&S, RPN matrix,... FDA Food Defence Plan Builder, etc
- Developed and implemented by capable and trained team
- Comply with standards audited against like FSSC22000, BRCGS, SQF, IFS WW SEP...
What is the scope of a food defense threat assessment and mitigation plan?
Food defense plan should cover threats from the whole food supply chain, supply chain of raw materials,... the site, as well as the supply chain of end products.
Those who are determined to cause harm and food attacks, are likely to attack the food business and the food supply chain wherever they can, it can be at primary food production stage, food transportation, food storage and warehousing, processing and manufacturing as well as retail and hospitality. There are lots of food defence attacks examples that can be discussed and considered. A good number of which is covered in the recorded Demo included with the Food Surety Food Defense programme example.
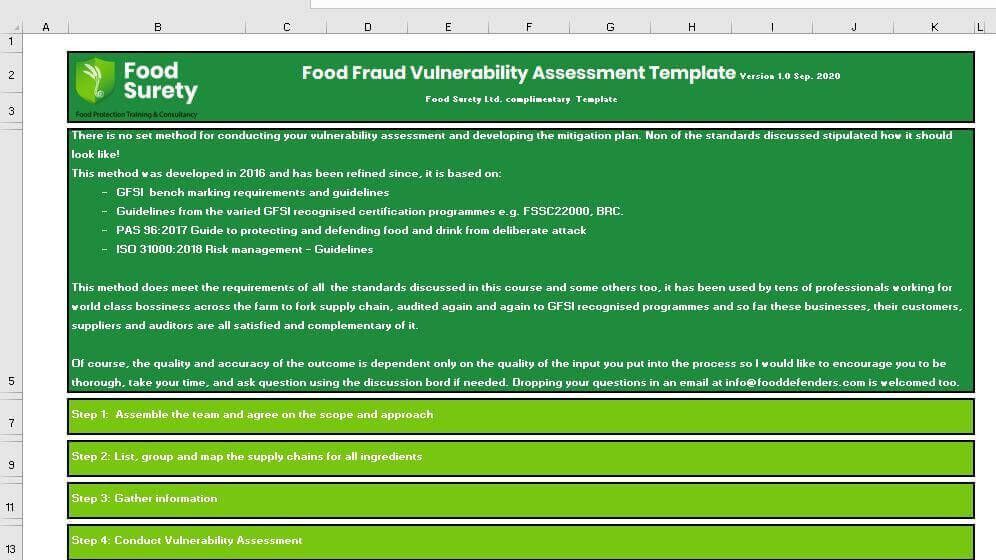
How to develop a food defence plan?
- Systematically identifying and documenting food defense threats
- Conducting threats assessment using a suitable tool/approach
- Implement and manage your food defence plan.
What food defence requirements does food Surety food defence - TACCP methods and template meet?
How does this food defence plan compare to The FDA's Food Defense Plan Builder (FDPB) version 2.0?
This template is built in a way to capture all the elements covered in The Food Defense Plan Builder (FDPB) version 2.0. While it is structured differently, it covers all aspects of the FDA Intentional adulteration Rule and beyond, it is actually more comprehensive and broader in line with GFSI guidelines. It complies with The Food Safety Modernization Act (FSMA) in USA addressing intentional adulteration and Food Defense.
Who might want to deliver an intentional attack on food business? Who are these attackers?
There are many different types of attackers out there, their motivation, access to the site and product and capability to deliver the food defense attack vary.
Here are the key categories of attackers:
- The extremist
- The opportunist
- The irrational individual
- The extortionist
- The disgruntled individual
- Professional criminals.